How to Create SSH Keys and Setup SSH Passwordless Authentication in Linux
Overview:
This guide shows how to create SSH (Secure Shell) private and public keys and use them to connect to a remote Linux system.
Page Contents
SSH Password Authentication and its Problems
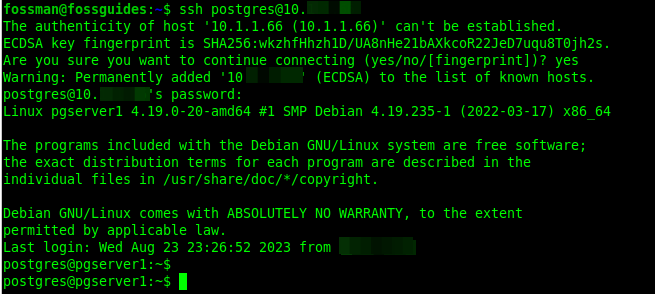
SSH is a popular and secure remote access and file transfer protocol used to access and administer a computer remotely. By default, SSH uses password authentication, where a user who has an account on the remote computer can use their username and the IP address or domain name of the computer to access it, like this:
$ssh [options] postgres@10.1.0.66 OR $ssh [options] postgres@pgserver1.example.com
After running the above ssh command, the user will be prompted to enter their password for authentication. If the password they have provided is correct and valid, the system will grant them access to resources such as the shell (to run commands) or the file system (to access files and directories).
However, using SSH password authentication poses some security risks because the username and password are transmitted over the network in plain text, and hackers can easily retrieve the password with a “Man-In-The-Middle attack” inside a local network.
Therefore, passwords are simple to remember and use but are subject to brute-force attacks (especially short passwords), phishing, and human errors. Besides, long passwords can easily be forgotten. As a result, the use of passwords for SSH authentication is widely not recommended.
SSH Key-Based Authentication (Public Key Authentication)
SSH keys are authentication credentials that consist of a pair of files: a private key, or identity key, that should be kept secret and secure on your local computer, and a public key that should be stored as authorized keys on the remote computer(s), such as servers, you want to access.
The benefits of key-based authentication in SSH
- Keys allow for passwordless login, which helps you avoid typing errors.
- Keys are harder to guess or steal than passwords, making them more resistant to hacking.
- Private keys can be protected with a passphrase or password, and
- Keys enable the automation of tasks and workflows.
How to Create an SSH Key Pair
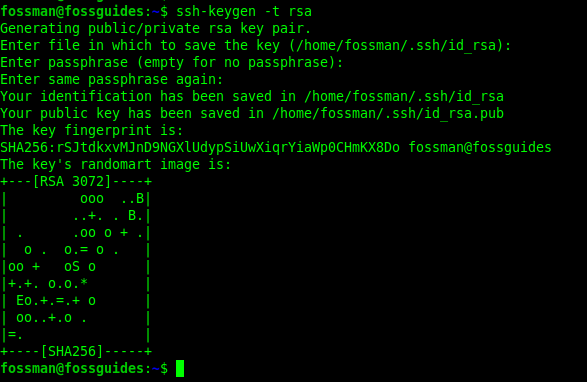
There are several types of keys you can create. For this guide, we will create an RSA key pair as follows: On your local Linux computer used for accessing remote Linux systems, open a terminal window and run the following ssk-keygen command to generate a key pair.
In this command, the -t flag is used to specify the key type, which is RSA in this case. Other possible values are “dsa”, “ecdsa”, or “ed25519”.
$ssh-keygen -t rsa
You will be prompted to supply a filename used to store the key pair, the default for rsa key type is id_rsa for the private key and id_rsa.pub for the public key. The key pairs are by default stored in the ~/.ssh directory in a user’s home directory.
However, while creating the key pair, you may provide any file name and location, and then supply the path name to the SSH client using the -i option.
You will also be prompted to enter a passphrase(or password) to protect your private key as shown in the following screenshot.
To specify the number of bits in the key, use the -b option as follows. For RSA keys, the minimum size is 1024 bits and the default is 2048 bits which is generally considered sufficient:
$ssh-keygen -t rsa -b 3072
Upload Public Key to Remote System
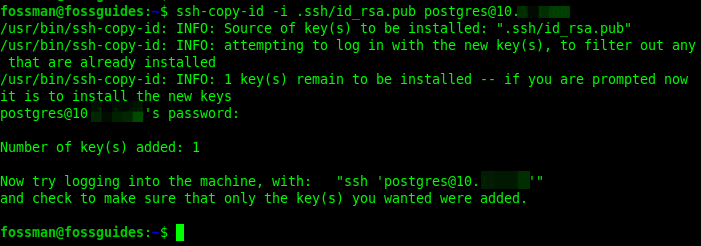
After generating the key pair, if you have access to the remote system, you can upload the public key into it using the ssh-copy command as follows. The -i option is used to specify the key file:
$ssh-copy-id -i id_rsa.pub postgres@10.1.0.66
Note: If you don’t have access to the remote system, share the public key (id_rsa.pub) via email or other secure means, with the system administrator of the remote system to install it in your account.
Use SSH Keys for Passwordless SSH Login
After setting up SSH passwordless authentication, you can use the private key to access the remote system as shown below. If your private is protected using a password/passphrase, you will be prompted to enter it:
$ssh -i .ssh/id_rsa postgre@10.1.0.66
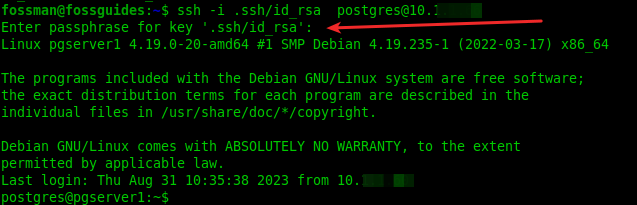
If the SSH passwordless authentication is working fine, you can disable password authentication on the remote system.
Conclusion
In this guide, we have explained the two methods of SSH authentication and looked at how to create SSH keys for passwordless SSH authentication in Linux. Using SSH keys for authentication has several advantages over passwords. And importantly, always remember to set a passphrase for your private key to secure it. To post a question or comment about this guide, use the feedback form below.