How to Fix the RETBleed Attack Warning in VirtualBox
Have you received the RETBleed Attack Warning in VirtualBox and are unsure how to resolve it? Then keep reading this guide. This warning appeared to me while I was running VirtualBox 7.0. Every virtual machine (VM) that I tried to boot displayed a warning. Some VMs booted normally a few seconds after the warning was shown, while others took a long time or just got stuck.
Here is the full error message, also captured in the screenshot.
[ 0.000000] RETBleed: WARNING: Spectre v2 mitigation leavers CPU vulnerable to RETBleed attacks, data leaks possible!
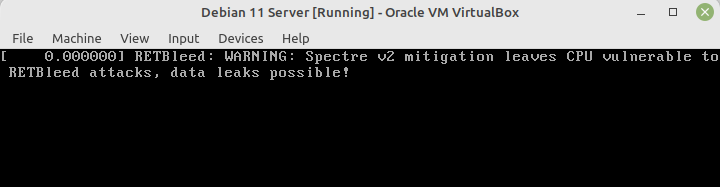
This warning is displayed each time you start a VM in VirtualBox. The reason is that by default Virtual Box disables the pertinent Spectre v2 mitigation, due to its performance hit on the CPU and system load.
Fix the RETBleed Attack Warning in VirtualBox
Run the following command on the host terminal. Make that you run this command with the permissions of the same user currently running the VirtualBox application. And ensure that the VM is fully shut down, not save-stated.
Do not forget to replace "Debian11" with the name of your VM. The command will not show any output if it runs successfully:
$VBoxManage modifyvm "Debian11" --spec-ctrl on
The --spec-ctrl command-line option is used in the preceding command to activate or deactivate the exposure of speculation control interfaces to the guest, assuming they are accessible on the host.
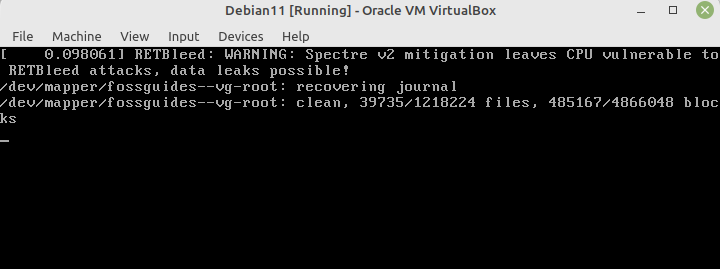
Once you have run the above commands, restart your VM and the warning should not show up anymore as shown in the following screenshot.
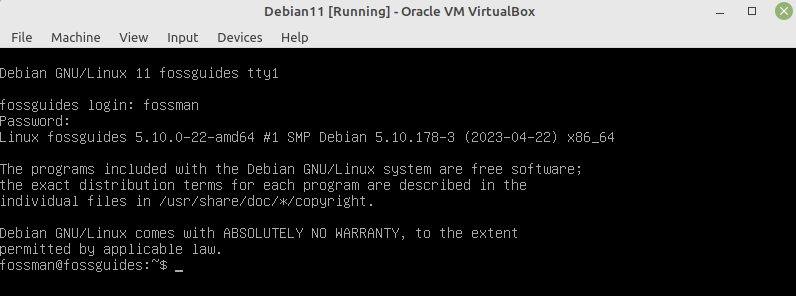
The next screenshot shows a successful boot process for the guest operating system.
To read more about this error, check out the RETBleed attack warning topic on the VirtualBox forum.
Conclusion
This post has shown you how to resolve the RETBleed attack warning in VirtualBox. As previously stated in this tutorial, enabling speculation control may greatly hamper performance depending on the host CPU and workload. Please use the feedback form below to share your opinions.